The Master File Table (MFT) is a critical artifact in digital forensics, especially when investigating Windows-based file systems. This guide delves into the structure, importance, and analysis of MFT to help forensic analysts uncover crucial evidence.
What is the Master File Table (MFT)?
The MFT is a core component of the NTFS (New Technology File System), which is the default file system for Windows operating systems. It acts as a database containing metadata about every file and directory on the volume. This includes details such as file name, size, creation time, modification time, and even information about deleted files.
Key Features of the MFT
- Comprehensive Metadata: Tracks essential attributes for each file and folder.
- Structure: Each file or directory corresponds to a record in the MFT, making it easier to analyze system activity.
- Sequential entry allocation: When a file is created, NTFS allocates the next available entry to record its information.
- Resilience: Even after deletion, file records persist in the MFT until the entry is reallocated.
Why is MFT Analysis Important?
MFT analysis is pivotal in digital forensics because it can:
- Reconstruct timelines: MFT timestamps reveal when files were created, accessed, or modified.
- Identify deleted or overwritten files: Remnants in the MFT may provide details about previously existing files, could be useful during data exfiltration cases for example.
- Uncover malicious activity: Attackers often create or modify files during exploitation; Threat actors can also manipulate timestamps to blend in; these changes are reflected in the MFT thanks to the multiple set of timestamps.
- Support file recovery: MFT entries can help locate the physical location of files on disk which would allow the investigator to recover the file.
Structure of the MFT
Each record in the MFT is 1024 bytes in size and contains several key attributes:
- Header (FILE Record Signature) – 0x46494C45: Identifies the record as an MFT entry with the signature “FILE”.
- Standard Information (SI) – 0x10: Contains timestamps and file attributes such as permissions.
- File Name (FN) – 0x30: Includes the file or directory name and its parent directory.
- Data – 0x80: Points to the actual file data on disk (or stores small files directly if the data size is less than 700 bytes).
Timestamps in MFT
During timeline analysis, the acronym MACB is often used and refers to:
- Modification Time: When the file content was last altered.
- Access Time: When the file was last opened or read.
- Changed Time: When the file’s MFT record was last updated.
- Birth Time: When the file was created.

Tools for MFT Analysis
Any can hex editor can be used to read the MFT but during an investigation but it is more efficient to use tools that can extract and parse the file. Below are some tools that could be used:
- FTK Imager: Can acquire and preview MFT entries.
- MFTECmd: Eric Zimmerman’s MFT Explorer Command Lines version parses and outputs results to different formats such csv.
- Sleuth Kit (TSK): Provides command-line utilities like fls and istat for extracting and analyzing MFT records.
Steps to Analyze the MFT
1. Extract the MFT
Use tools like FTK Imager to acquire the MFT file ($MFT) from the disk image. In a live environment, tools like KAPE can help extract the MFT without imaging the entire disk.
2. Parse the MFT
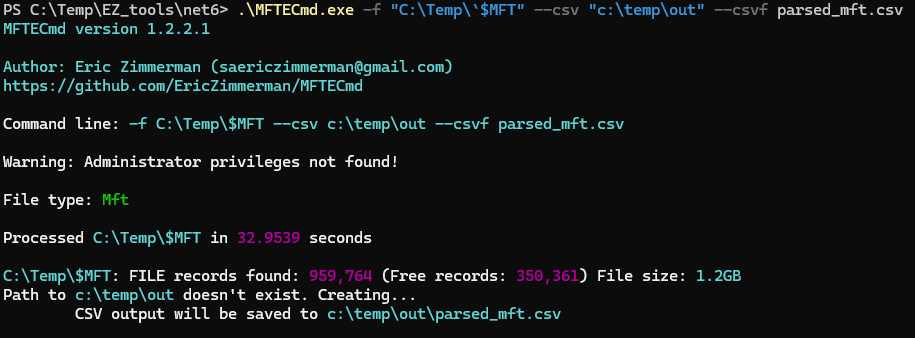
Feed the extracted MFT into a parsing tool to convert raw entries into readable data. For example, with MFTECmd:
MFTECmd.exe -f "C:\Temp`$MFT" --csv "c:\temp\out" --csvf parsed_mft.csv
-fspecifies the file to process--csvspecifies the directory to save CSV formatted results to--csvfspecifies the file name to save CSV formatted results to
3. Examine Key Attributes
Below is what the previously obtained output looks like in Timeline Explorer, only a few columns are displayed here for readability:
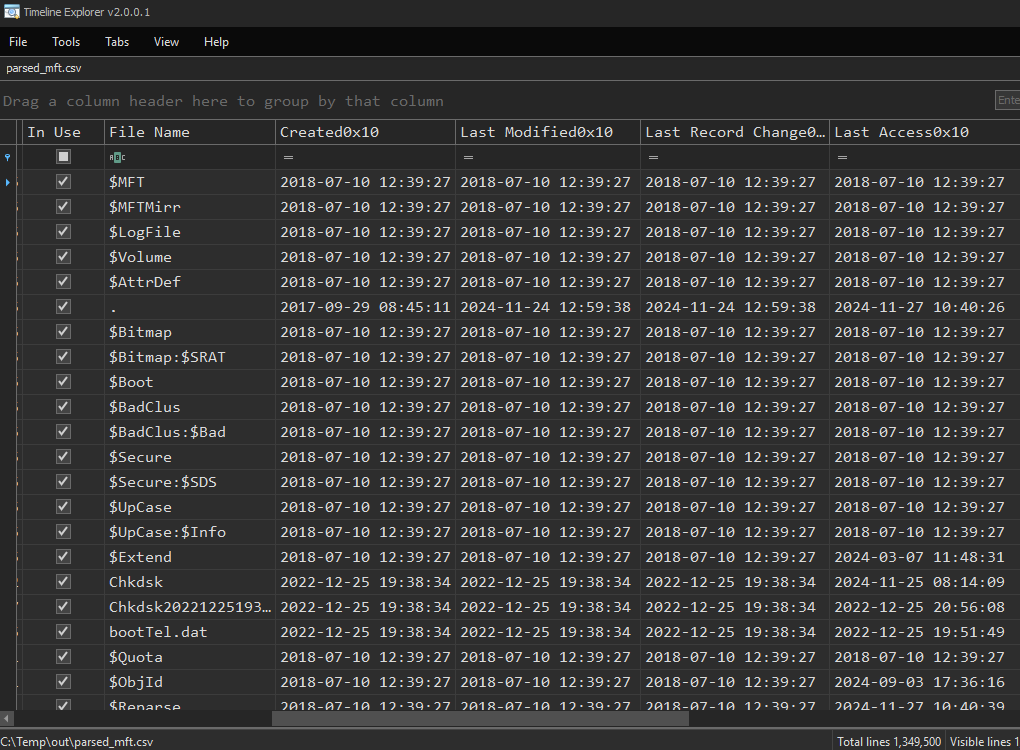
- File Timestamps: Look for anomalies, such as timestomping attempt
- File Names and Paths: Identify suspicious or hidden files.
- Deleted Files: Focus on records marked as deleted, as they may contain remnants of malicious activity.
- Alternate Data Stream (ADS): Identify additional information available such as Zone.Identifier or hidden data like malicious payload.
4. Correlate with Other Artifacts
Combine MFT data with logs, memory dumps, registry analysis or specialized artefacts to build a comprehensive view of the incident.
Challenges in MFT Analysis
- Timestamps Manipulation: Skilled attackers may alter timestamps to evade detection.
- Tip: Employ timeline correlation to identify anomalies even when timestamps are altered.
- Overwritten Entries: When the disk is heavily used, deleted MFT entries may be overwritten quickly.
- Tip: Use complementary artifacts like volume shadow copies for historical MFT snapshots.
- Partial Records: Corrupted or incomplete records may prevent file recovery.
- Tip: Use tools that perform file carving.
Conclusion
MFT analysis is an indispensable skill for digital forensic professionals. It provides a wealth of information about file system activity, enabling investigators to piece together what happened on a system. By mastering the structure, tools, and techniques for MFT analysis, analysts can uncover vital evidence in a wide range of cases including but not limited to data exfiltration, malware infection, unauthorized access.
