When the Security Operations team is engaged, it usually means that something may have happened and requires an intervention. And that needs to happen fast:
- John’s user account is compromised, the SecOps team needs to analyse all the hosts which John has access to.
- Alice is suspected of exfiltrating confidential data to an external platform.
- The SecOps team suspects that attackers have disabled the EDR.
- A CISA report warns that multiple threat actors have been actively exploiting a software vulnerability. The SecOps team is aware that one publicly exposed server was vulnerable and has only recently been patched. SecOps wants to make sure there is no sign of vulnerability exploitation on that server.
Why is your shiny software not enough?
- Limited visibility: Only assets on which your tools are deployed can be analysed.
- Limited capability: Relying on black box commercial tools limits analysis to what capability the vendor offers (lack of the functionality to scale artefact collection for example).
- Limited reliability: Security tools can be disabled by the attackers which will reduce detection and triage capabilities.
KAPE to the rescue !
KAPE is a software that collects targeted files on a host and can also run third party programs (e.g., to process the collected files !). It has been created by Eric Zimmerman.
During investigation, analysts may need to collect:
- evidences of execution
- evidences of download
- suspicious/malicious files
- registry hives
- etc
KAPE is the response to fast artefact collection. It allows analysts to quickly gather the files needed for the ongoing investigation without having to remember all the different artefact location and without the gather them manually one by one.
Modules are also a great feature. Indeed, collected files in their raw form may not always be useful as it is, such as prefetch or lnk files. Modules allows analysts to setup external binaries to run and in this context it could be parsers. So we would collect and parse directly the targeted artefacts so that KAPE output is ready to be analysis.
KAPE comes with a huge list of target and modules files ! So you do not need to worry about any configurations as you start playing with KAPE.
How to collect a file
KAPE target files (tkape) are used to define parameters primarily based around file paths on a given volume.
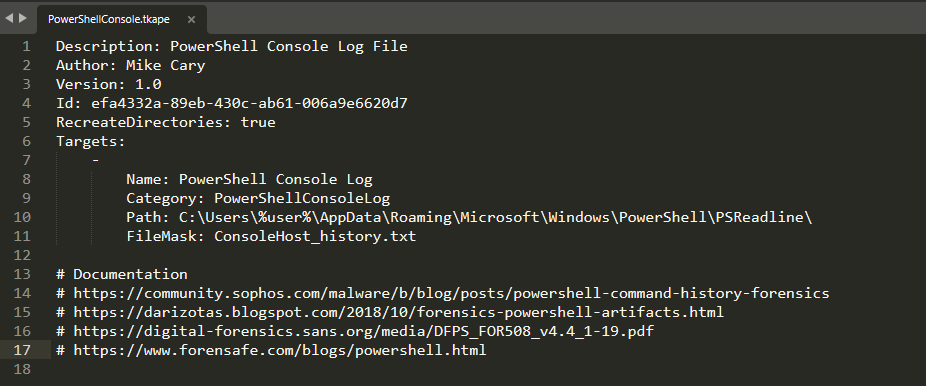
Above is the .tkape file for the PowerShell console log which sits in C:\Users\%user%\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine and the target file is called ConsoleHost_history.txt.
Using KAPE to collect the target is straightforward. In the example below Kape will search –tsource which is the whole C: drive for the specified –target PowerShellConsole history file:
- kape.exe –tsource C: –target PowerShellConsole –tdest “c:\programdata\kape_output”
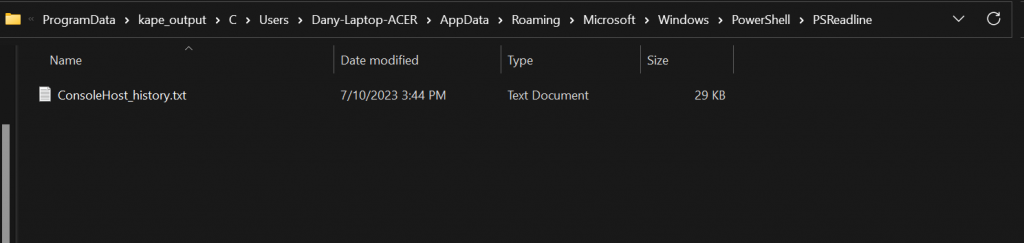
The file is copied into the specified target destination --tdest “C:\Programdata\kape_output”. By default, Kape recreates the source path where it found the file in the destination directory. This behaviour is defined in the target file.
How to execute a module
Modules work in a similar fashion to targets in that they look for certain types of files, but rather than copy them somewhere else, a Module’s job is to run programs against files, (e.g, parsing artefact to csv or text that can then be reviewed by an examiner). Modules have an .mkape extension.
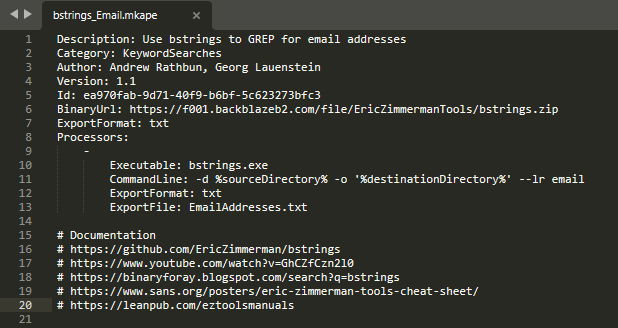
To run the module bstrings_Email that will search for email addresses in each files located in C:\test\ and direct the output to C:\test\output\ :
- .\kape.exe –msource C:\test\ –module bstrings_Email –mdest C:\test\output
How to get KAPE ?
- You can download KAPE on Kroll’s website.
- The full documentation can be found Eric Zimmerman’s GitHub.