LNK files (shortcuts) are a treasure trove of forensic evidence, often overlooked in investigations. Found ubiquitously in Windows environments, these files can reveal details about file usage, paths, and associated applications. In this article, we’ll explore methods for collecting and analysing LNK files, providing insights into their forensic value and practical steps to extract critical information.
Understanding the Role of LNK Files in Forensics
LNK files are Windows shortcut files that link to executables, documents, folders, or remote shares. They are automatically created under certain conditions, such as when a file is opened from specific locations, pinned to the taskbar, or accessed via recent files.
LNK files can also be used by malicious actors by linking the shortcut to a malicious file or network location.
The analysis of LNK files can provide:
- File metadata: timestamps, size, and original path.
- User interaction details: access history, volume information, and network resource usage.
- Evidence of remote or deleted files.
Their forensic relevance lies in their persistence even after the linked file is moved or deleted, offering investigators a crucial timeline of user activity.
Collection Techniques for LNK Files
1. File System Search
To locate LNK files, investigators should search the user profile directories where shortcuts are commonly stored:
%AppData%\Microsoft\Windows\Recent%UserProfile%\Desktop%UserProfile%\Links- etc
A broader search across the file system using a forensic toolkit can reveal hidden or misplaced LNK files. Tools like Autopsy, FTK Imager or KAPE support filtering by the .lnk extension, expediting this process.
2. Memory Analysis
Memory dumps may contain transient LNK file information not stored on disk. Volatility or MemProcFS frameworks can be employed to carve relevant data from a memory image.
3. Network Shares and Removable Media
LNK files may be created for shortcuts to network drives or USB devices. Forensic investigators should inspect connected media history and mount points, which can provide critical context about the device usage.
Parsing LNK Files
1. Manual Examination
A hex editor can be used to inspect the raw binary structure of an LNK file. The format is well-documented by Microsoft, allowing for the extraction of key information such as:
- Header information: target GUID and flags.
- Link target ID list: path and metadata.
- Extra data blocks: network volume information and Tracker data.
- And much more
2. Automated Tools
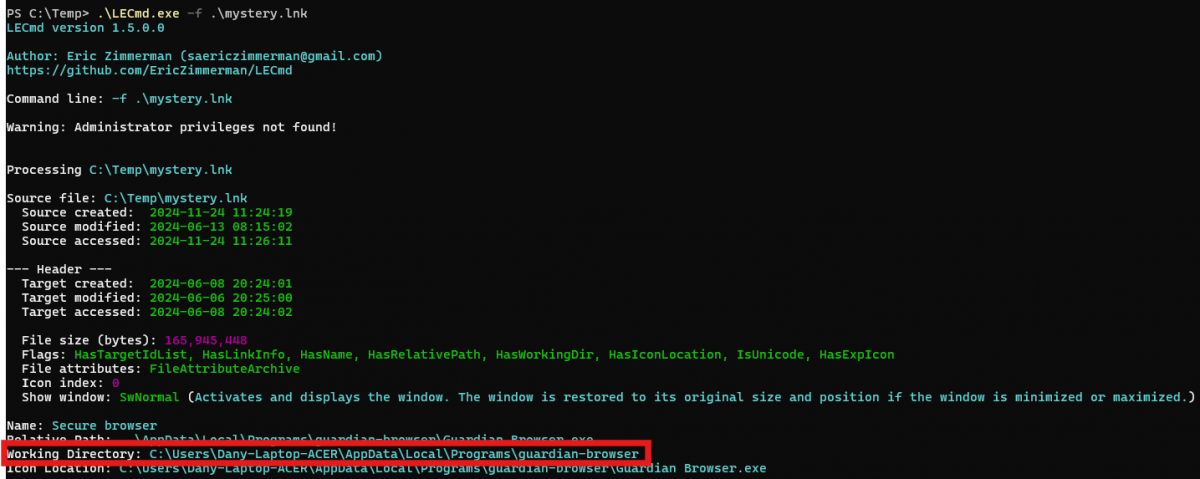
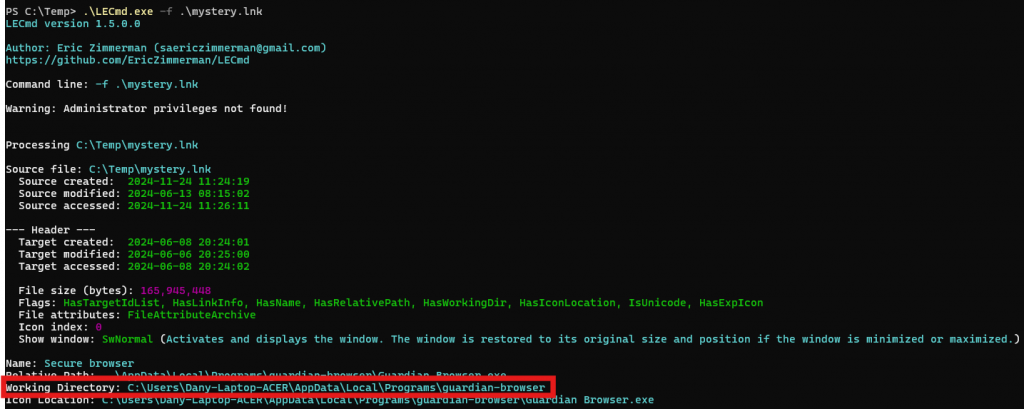
To accelerate the analysis, tools like Eric Zimmerman’s LECmd or LnkParse3 can decode LNK file content efficiently. These tools extract and present data such as:
- File creation, access, and modification timestamps.
- Target file location (absolute and relative paths).
- Network share details, if applicable.
Parsing a LNK file with LECmd is simple:
Below, some other functionalities such as parsing all LNK files in a directory and writing the output to a CSV file (that could then be viewed with Timeline Explorer for example):
3. Correlation with Other Artefacts
LNK files gain more context when correlated with other data sources, such as prefetch files, registry entries, or event logs. This cross-referencing can confirm user activity and intent.
Interpreting Results
Interpreting the data extracted from LNK files requires an understanding of user habits, system configuration, and operational context. For instance:
- A deleted file referenced in an LNK file may indicate malicious activity or user attempts to conceal evidence.
- Network paths in LNK files can hint at unauthorised access to shared resources or redirection to an remote server controlled by the attacker
- Analysis of timestamps can reveal patterns of access or usage that might align with specific incidents.
Conclusion
LNK file analysis is a cornerstone of forensic investigations in Windows environments. By leveraging both manual and automated techniques, investigators can extract rich contextual information from these artefacts. When combined with other sources of evidence, LNK files provide a clear window into user activity, helping to unravel complex cases.
Forensic practitioners should integrate LNK file analysis into their workflow, ensuring no detail goes unnoticed in the pursuit of truth.